Published
Weekend Reading — When toasters attack
Design Objective
How the Web Became Unreadable "I thought my eyesight was beginning to go. It turns out, I’m suffering from design."
Tools of the Trade
google/highwayhash Addressing performance and security, this package includes a faster version of SipHash, a data-parallel variant of SipHash using tree hashing, and an even faster algorithm called HighwayHash.
Books Programmers Don't Really Read
Please stop recommending books to others that you haven't read yourself. It's counter productive, as often there is a better book (more focused on a specific problem domain, easier to understand, geared more toward a specific programming language or programming skill level) that someone more knowledgeable could recommend.
Just passed a license plate that said "LGTM +1" on the freeway. I love you, Silicon valley.
Lingua Scripta
Tips for using async functions (ES2017) Few things you should know when using async/await.
npm v4.0.0 Hoping 4.x will be stable and dependable, and cure our 3.x blues.
Loop through a collection of DOM elements Old tricks for old browsers (that are still in circulation).
Lines of Code
Many people underestimate the importance of deleting unnecessary code, it still has to be read and understood.
Use whatever brace style you prefer.
But not this.
Don't do this.
Seek help instead of this.
Devoops
OH: I lived in a house with two other women engineers and at some point our PagerDuty cycles synced up.
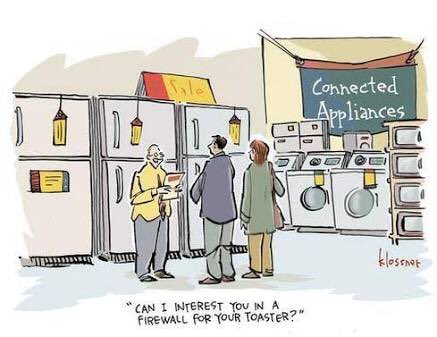
In a relatively short time we've taken a system built to resist destruction by nuclear weapons and made it vulnerable to toasters.
Locked Doors
Hacked Cameras, DVRs Powered Today’s Massive Internet Outage Most people have no idea their connected devices are compromised within minutes of being powered on:
Mirai scours the Web for IoT devices protected by little more than factory-default usernames and passwords, and then enlists the devices in attacks that hurl junk traffic at an online target until it can no longer accommodate legitimate visitors or users.
And there's nothing you can do about it, other than throwing these devices in the trash:
That’s because while many of these devices allow users to change the default usernames and passwords on a Web-based administration panel that ships with the products, those machines can still be reached via more obscure, less user-friendly communications services called “Telnet” and “SSH.”
Also, an attempt to identify the device makers.
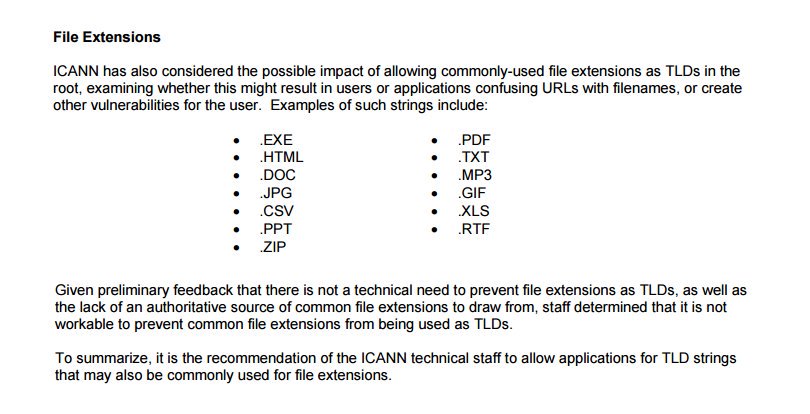
Matthew Olney Security experts: "using common file extensions as TLDs is a bad idea" ICANN: ¯_(ツ)_/¯
“Most serious” Linux privilege-escalation bug ever is under active exploit (updated) "A serious vulnerability that has been present for nine years in virtually all versions of the Linux operating system is under active exploit". Nine years.
"How'd your accounts get owned?"
"Toaster. You?"
"Washing machine."
Techtopia
Little known fact: inventors of BlueTooth were wabi sabi fetishists — felt reliable functioning would undermine ephemeral beauty of life.
black mirror #3 set in the distant future where you can attach a video to an email and it actually works
None of the Above
@tenderlove "Area man approves pull request"

Mexico’s Demand For Potent California Marijuana Creates Southbound Smuggling The times are changing.
In Silicon Valley, some principles do matter: Efficiency, Respect, and Communication. California is for sure the “Land of The Cool”. But don’t get it wrong. Things are codified.


