Published
Weekend Reading — Ravioli Oriented Architecture
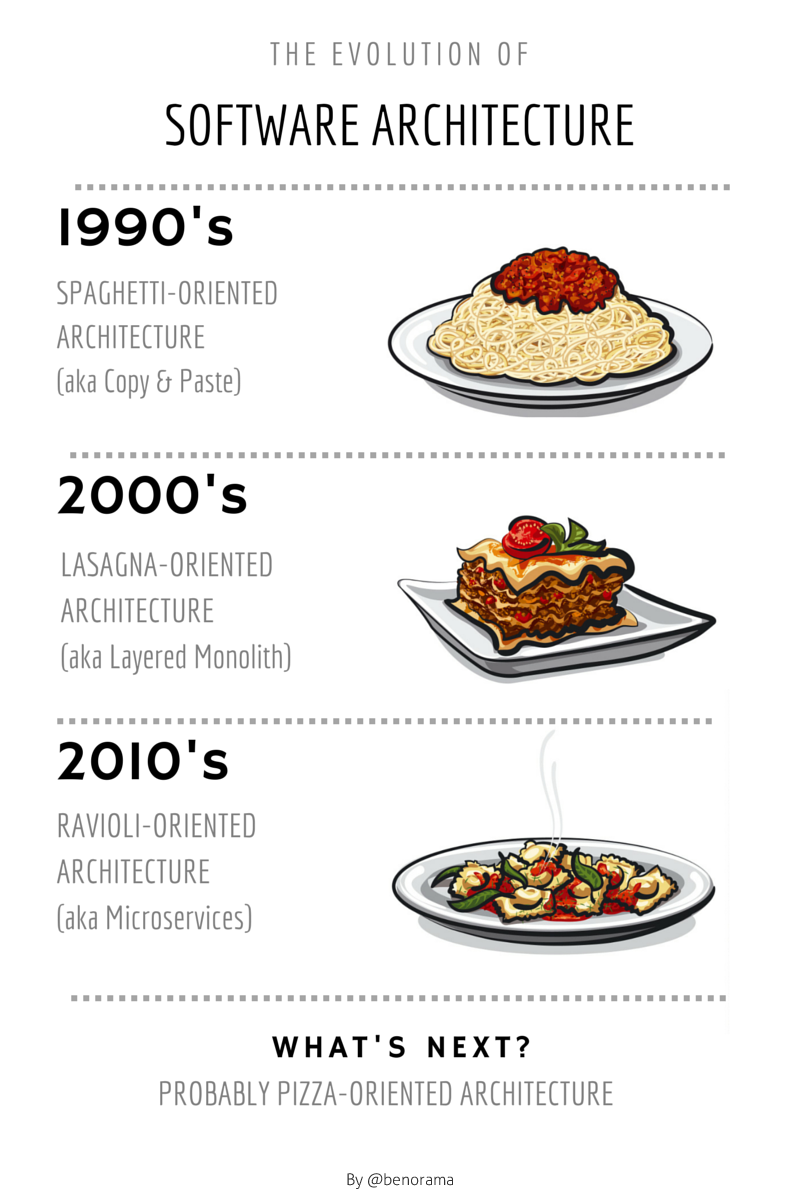
The evolution of software architecture
Design Objective
I don’t think this effect is limited to the products in the physical world. There’s a mental butt-brush effect, and it happens every time that a software product makes its’ customers feel awkward, clumsy, or stupid.
...
Customers who feel stupid don’t buy. They find excuses not to use, and not to switch.
And the users exclaimed with a laugh and a taunt: "It's just what we asked for but not what we want."
Tools of the Trade
Note: Please proofread your resume. Dockers are very different from Docker.
asciinema This is just awesome in so many ways. Easy CLI tool for recording terminal sessions and sharing them on the web. Embeds like a video, but it renders text, so looks great at any resolution, and lets you copy & paste.
Bootcards A cards-based UI with dual-pane capability for mobile and desktop, built on top of Bootstrap.
the-art-of-command-line Master the command line, in one page.
It may be possible to write a post criticising agile without giving off a strong “I’m too good for this” smell, but nobody’s managed it yet.
DRIFT And in that spirit, introducing DRIFT, the "do whatever, whenever" development methodology:
How do you get started with DRIFT ?
- Make a list of tasks
- Tackle tasks as and when you want
- Add other tasks as they occur to you
- Drift in the current of your productivity
Working in quantum computing tech support is gonna be a severe PITA: "Have you tried turning it off, and on, at the same time???"
Lingua Scripta
ECMAScript 2015 is now an Ecma Standard Congratulations.
javascript.com Also, JS gets its own domain.
WebAssembly: a binary format for the web Introducing a new binary format for asm.js, which will make it easier to write JavaScript in every language but JavaScript.
Is it CrossFit or JavaScript? Hmmm …
Lines of Code
Reusability Trap Sustrik's law:
In a long-lived project, components are being replaced. Nice reusable components are easy to replace and so they are. Ugly non-reusable components are pain to replace and each replacement means both a considerable risk and considerable cost. Thus, more often then not, they are not replaced. As the years go by, reusable components pass away and only the hairy ones remain. In the end the project turns into a monolithic cluster of ugly components melted one into another.
This mechanism seems to account for most of the complexity in legacy codebases.
Let's call it Sustrik's law:
"Well-designed components are easy to replace. Eventually, they will be replaced by ones that are not so easy to replace."
Devoops
An Inside Look at Facebook’s Approach to Automation and Human Work
But these are really dumb things – things that are really, really trivial to automate. And thereby, it allows us to take that engineer we really worked hard to recruit, and trained to deal with higher-level things, away from doing something pretty remedial – work that is not fun, and they’re not growing or learning anything, yet it’s time consuming – and say: “Hey, help us figure out how to architect this new service. Go figure out how to make this thing run faster, or help build this new automation to tackle the challenges we have in mobile applications. Help us design our new data center.”
Peopleware
Contributor Covenant A code of conduct for open source projects. If your project has any participation policy — coding convention, contributing guidelines, etc — why no code of conduct?
There are only two hard problems in social discourse: Experience invalidation, and naming things.
Inside Obama's Stealth Startup In which the Obama administration decides to take tech seriously, hire top talent, and fix our broken systems. Including, making all works available to the public domain, and agile delivery methods:
Publish a repository consisting of all prototype source code, design assets, and all associated documentation that went into the creation of the prototype, to an online and publicly accessible version control system (e.g., GitHub, GitLab, BitBucket) that supports git. The uploaded repository shall be in git. Posting a repository in a different version control system will not be accepted.
Locked Doors
How to hack into an email account, just by knowing your victim's mobile number The problem with verification codes as password alternatives is that they're incredibly easy to social engineer.
Serious OS X and iOS flaws let hackers steal keychain, 1Password contents From the category of vulnerabilities known as Cross-App Resource Access, or XARA. I sense we'll see more of these in the future. As always, AgileBits has an insightful writeup on their blog.
How DuckDuckGo Rode A Wave Of Post-Snowden Anxiety To Massive Growth 600% growth over the past two years, as more people realize privacy is an opt-in, not a default.
Encryption “would not have helped” at OPM, says DHS official
… the Unix systems administrator for the project "was in Argentina and his co-worker was physically located in the [People's Republic of China]. Both had direct access to every row of data in every database: they were root.
Stuxnet spawn infected Kaspersky using stolen Foxconn digital certificates
… raises troubling questions about the reliability of the entire digital certificate mechanism that Microsoft, Apple, and most other software makers rely on to establish the legitimacy of applications and drivers.
None of the Above

Move over, Turing In which the author gives the Rorschach test to four AI software and then analyzes their personality.
I'll raise a glass to the first news site that ever has a home page that says "nothing much happened today in this field"
The Rise and Fall of Two Florida Stoners Who Made It Big as Gunrunners Florida man x2.
It's kinda ironic when you're watching a show about building a compression program for great streaming quality and it won't stream
@Atheistican "Hey... If you're going to shave a cat, this is how you do it."

